- ASCs
-
How We Help ASCs
-
Solutions
ASC SoftwareDelivered on a single platform in the cloud, SIS Complete simplifies ASC operations from start to finish.
Revenue Cycle ServicesAccelerate your revenue cycle with tech-enabled billing, coding, and transcription solutions delivered by our team of RCM experts.
ComplianceSimply compliance management with SIS Comply, a comprehensive, easy-to-use solution purpose-built for ASCs.
- ASC Software
- Revenue Cycle Services
- Compliance
-
- Hospitals
- Who We Are
- Resources
- Careers We’re Hiring!
- Contact Us
- Log In
-
{{ request.remote_ip }}
{{ request.full_url }}
{{ page_meta.html_title }}
-
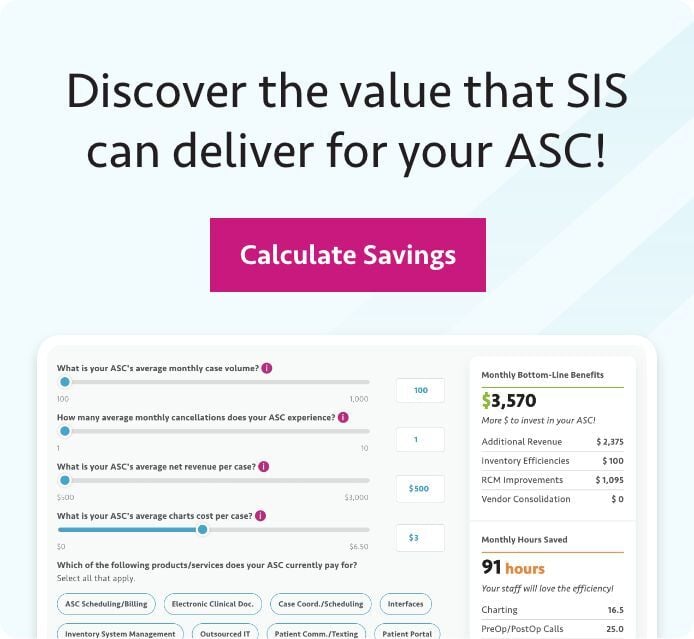
Using Tech and Innovation ASC Revenue Cycle Management
Forward-thinking ASCs can use modern technology, including AI and automation, to protect and grow revenue. Gain a clear framework for selecting and deploying new solutions, preparing staff and partners for change, and strengthening revenue cycle performance.
 What's Next for the ASC Industry? SIS and industry experts discuss current challenges and future opportunities for ASCs, providing actionable recommendations and best practices to drive growth, efficiency, and quality outcomes.
What's Next for the ASC Industry? SIS and industry experts discuss current challenges and future opportunities for ASCs, providing actionable recommendations and best practices to drive growth, efficiency, and quality outcomes.
















.png?width=300&name=2024_SIS_BLOG_CYBERATTACK%20(1).png)